| Problem | Solution |
|---|---|
 |
  
Symmetry: None
|
 |
    |
 |
       |
 |
   |
 |
  |
 |
       |
 |
    |
 |
         |
 |
   |
 |
     |
 |
 |
 |
  |
 |
  |
 |
  |
 |
   |
 |
     |
 |
    |
 |
 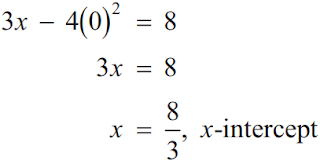   |
Forget Metasploit: Inside Predator’s Zero-Click Advertising-Driven Phone
Hacking System
-
The Intellexa Leaks have transformed Predator from a partially understood
“mercenary spyware product” into a clearly mapped, industrial-grade
offensive s...
2 weeks ago








0 comments:
Post a Comment